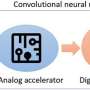
In the modern era, there has been explosive growth in the demand for computing power for cognitive image and video processing. While convolutional neural networks offer improved performance for image processing, they also come with a significant increase in power consumption and memory requirements.In the modern era, there has been explosive growth in the demand for computing power for cognitive image and video processing. While convolutional neural networks offer improved performance for image processing, they also come with a significant increase in power consumption and memory requirements.[#item_full_content]
New research from the University of Montana and its partners suggests artificial intelligence can match the top 1% of human thinkers on a standard test for creativity.New research from the University of Montana and its partners suggests artificial intelligence can match the top 1% of human thinkers on a standard test for creativity.[#item_full_content]
Computer scientists at the University of Massachusetts Amherst recently found that data-visualization experts have no agreed-upon understanding of who makes up one of their largest audiences—novice users. The work, which recently won a coveted Best Paper Award at the Association for Computing Machinery’s conference on Human Factors in Computing Systems (ACM CHI), is an important first step in ensuring more inclusive data visualizations, and thus data visualization that works for all users.Computer scientists at the University of Massachusetts Amherst recently found that data-visualization experts have no agreed-upon understanding of who makes up one of their largest audiences—novice users. The work, which recently won a coveted Best Paper Award at the Association for Computing Machinery’s conference on Human Factors in Computing Systems (ACM CHI), is an important first step in ensuring more inclusive data visualizations, and thus data visualization that works for all users.[#item_full_content]
In the evolving relationship between technology and society, humans have shown themselves to be incredibly adaptable. What once left us breathless, soon becomes integrated into our everyday lives.In the evolving relationship between technology and society, humans have shown themselves to be incredibly adaptable. What once left us breathless, soon becomes integrated into our everyday lives.[#item_full_content]
Generative AI tools such as Midjourney, Stable Diffusion and DALL-E 2 have astounded us with their ability to produce remarkable images in a matter of seconds.Generative AI tools such as Midjourney, Stable Diffusion and DALL-E 2 have astounded us with their ability to produce remarkable images in a matter of seconds.[#item_full_content]
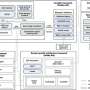
Co-design, that is, designing software and hardware simultaneously, is one way of attempting to meet the computing-power needs of today’s artificial intelligence applications. Compilers, which translate instructions from one representation to another, are a key piece of the puzzle. A group of researchers at the Chinese Academy of Sciences summarized existing compiler technologies in deep learning co-design and proposed their own framework, the Buddy Compiler.Co-design, that is, designing software and hardware simultaneously, is one way of attempting to meet the computing-power needs of today’s artificial intelligence applications. Compilers, which translate instructions from one representation to another, are a key piece of the puzzle. A group of researchers at the Chinese Academy of Sciences summarized existing compiler technologies in deep learning co-design and proposed their own framework, the Buddy Compiler.[#item_full_content]
In a new study, researchers from Université libre de Bruxelles demonstrate the potential of blockchain technology, known from cryptocurrencies such as Bitcoin and Ethereum, to secure the coordination of robot swarms. In experiments conducted with both real and simulated robots, they show how blockchain technology enables a robot swarm to neutralize harmful robots without human intervention, thus enabling the deployment of autonomous and safe robot swarms. Their work is published in the journal Science Robotics.In a new study, researchers from Université libre de Bruxelles demonstrate the potential of blockchain technology, known from cryptocurrencies such as Bitcoin and Ethereum, to secure the coordination of robot swarms. In experiments conducted with both real and simulated robots, they show how blockchain technology enables a robot swarm to neutralize harmful robots without human intervention, thus enabling the deployment of autonomous and safe robot swarms. Their work is published in the journal Science Robotics.[#item_full_content]
When real-world disasters occur, logistics play a crucial role in emergency disaster management. Emergency material scheduling is a vital piece of the emergency logistics plan. Having a reasonable and efficient emergency material scheduling plan is essential in order to save lives and reduce property losses.When real-world disasters occur, logistics play a crucial role in emergency disaster management. Emergency material scheduling is a vital piece of the emergency logistics plan. Having a reasonable and efficient emergency material scheduling plan is essential in order to save lives and reduce property losses.[#item_full_content]
Chart captions that explain complex trends and patterns are important for improving a reader’s ability to comprehend and retain the data being presented. For people with visual disabilities, the information in a caption often provides their only means of understanding the chart.Chart captions that explain complex trends and patterns are important for improving a reader’s ability to comprehend and retain the data being presented. For people with visual disabilities, the information in a caption often provides their only means of understanding the chart.[#item_full_content]
Even though our computers are now better than 15 years ago, they still malfunction 11%–20% of the time, a new study from the University of Copenhagen and Roskilde University concludes. The researchers behind the study therefore find that there are major gains to be achieved for society by rethinking the systems and involving users more in their development.Even though our computers are now better than 15 years ago, they still malfunction 11%–20% of the time, a new study from the University of Copenhagen and Roskilde University concludes. The researchers behind the study therefore find that there are major gains to be achieved for society by rethinking the systems and involving users more in their development.[#item_full_content]