Powerful artificial intelligence (AI) systems, like ChatGPT and Gemini, simulate understanding of comedy wordplay, but never really “get the joke,” a new study suggests.Powerful artificial intelligence (AI) systems, like ChatGPT and Gemini, simulate understanding of comedy wordplay, but never really “get the joke,” a new study suggests.[#item_full_content]
A new Australian study has smashed the myth that generative AI systems such as ChatGPT could soon replace society’s most creative playwrights, authors, songwriters, artists and scriptwriters.A new Australian study has smashed the myth that generative AI systems such as ChatGPT could soon replace society’s most creative playwrights, authors, songwriters, artists and scriptwriters.[#item_full_content]
You’ve just put a dollar into a machine to play a song and it stopped playing after a few seconds. You put in another dollar and the tune stops after a minute. You can’t get your dollars back and can’t listen to the song you want. But what if you had known ahead of time what would happen, and could have saved yourself the money and frustration?You’ve just put a dollar into a machine to play a song and it stopped playing after a few seconds. You put in another dollar and the tune stops after a minute. You can’t get your dollars back and can’t listen to the song you want. But what if you had known ahead of time what would happen, and could have saved yourself the money and frustration?[#item_full_content]
Soon, researchers may be able to create movies of their favorite protein or virus better and faster than ever before. Researchers at the Department of Energy’s SLAC National Accelerator Laboratory have pioneered a new machine learning method—called X-RAI (X-Ray single particle imaging with Amortized Inference)—that can “look” at millions of X-ray laser-generated images and create a three-dimensional reconstruction of the target particle. The team recently reported their findings in Nature Communications.Soon, researchers may be able to create movies of their favorite protein or virus better and faster than ever before. Researchers at the Department of Energy’s SLAC National Accelerator Laboratory have pioneered a new machine learning method—called X-RAI (X-Ray single particle imaging with Amortized Inference)—that can “look” at millions of X-ray laser-generated images and create a three-dimensional reconstruction of the target particle. The team recently reported their findings in Nature Communications.[#item_full_content]
By studying the theoretical limits of how light can be used to perform computation, Cornell researchers have uncovered new insights and strategies for designing energy-efficient optical computing systems.By studying the theoretical limits of how light can be used to perform computation, Cornell researchers have uncovered new insights and strategies for designing energy-efficient optical computing systems.[#item_full_content]
Hospitals do not always have the opportunity to collect data in tidy, uniform batches. A clinic may have a handful of carefully labeled images from one scanner while holding thousands of unlabeled scans from other centers, each with different settings, patient mixes and imaging artifacts. That jumble makes a hard task—medical image segmentation—even harder still. Models trained under neat assumptions can stumble when deployed elsewhere, particularly on small, faint or low-contrast targets.Hospitals do not always have the opportunity to collect data in tidy, uniform batches. A clinic may have a handful of carefully labeled images from one scanner while holding thousands of unlabeled scans from other centers, each with different settings, patient mixes and imaging artifacts. That jumble makes a hard task—medical image segmentation—even harder still. Models trained under neat assumptions can stumble when deployed elsewhere, particularly on small, faint or low-contrast targets.[#item_full_content]
IT-Security Researchers from the University of Vienna and SBA Research identified and responsibly disclosed a large-scale privacy weakness in WhatsApp’s contact discovery mechanism that allowed the enumeration of 3.5 billion accounts. In collaboration with the researchers, Meta has since addressed and mitigated the issue.IT-Security Researchers from the University of Vienna and SBA Research identified and responsibly disclosed a large-scale privacy weakness in WhatsApp’s contact discovery mechanism that allowed the enumeration of 3.5 billion accounts. In collaboration with the researchers, Meta has since addressed and mitigated the issue.[#item_full_content]
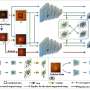
A new AI-driven technology developed by researchers at UNIST promises to significantly reduce data transmission loads during image transfer, paving the way for advancements in autonomous vehicles, remote surgery and diagnostics, and real-time metaverse rendering—applications that demand rapid, large-scale visual data exchange without delay.A new AI-driven technology developed by researchers at UNIST promises to significantly reduce data transmission loads during image transfer, paving the way for advancements in autonomous vehicles, remote surgery and diagnostics, and real-time metaverse rendering—applications that demand rapid, large-scale visual data exchange without delay.[#item_full_content]
New research from the University of Waterloo is making inroads on one of the biggest problems in theoretical computer science. But the way to do it, according to Cameron Seth, a Ph.D. researcher working in the field of algorithmic approximation, is by breaking the problem down into smaller pieces.New research from the University of Waterloo is making inroads on one of the biggest problems in theoretical computer science. But the way to do it, according to Cameron Seth, a Ph.D. researcher working in the field of algorithmic approximation, is by breaking the problem down into smaller pieces.[#item_full_content]
In his research, Professor Marko Huhtanen from the University of Oulu, who specializes in applied and computational mathematics, introduces a new method for compressing images. This technique combines several well-known compression methods, leveraging their best features. The study has been published in IEEE Signal Processing Letters.In his research, Professor Marko Huhtanen from the University of Oulu, who specializes in applied and computational mathematics, introduces a new method for compressing images. This technique combines several well-known compression methods, leveraging their best features. The study has been published in IEEE Signal Processing Letters.[#item_full_content]