In the 17th century, German astronomer Johannes Kepler figured out the laws of motion that made it possible to accurately predict where our solar system’s planets would appear in the sky as they orbit the sun. But it wasn’t until decades later, when Isaac Newton formulated the universal laws of gravitation, that the underlying principles were understood.In the 17th century, German astronomer Johannes Kepler figured out the laws of motion that made it possible to accurately predict where our solar system’s planets would appear in the sky as they orbit the sun. But it wasn’t until decades later, when Isaac Newton formulated the universal laws of gravitation, that the underlying principles were understood.[#item_full_content]
A new system developed by Cornell Tech researchers helps users detect when their online accounts have been compromised—without exposing their personal devices to invasive tracking by web services.A new system developed by Cornell Tech researchers helps users detect when their online accounts have been compromised—without exposing their personal devices to invasive tracking by web services.[#item_full_content]
A novel algorithmic system that works subtly in the background to mutual benefit, and adapts quickly to local conditions, could be useful in data processing where noise terms can be replaced with useful estimates of their values.A novel algorithmic system that works subtly in the background to mutual benefit, and adapts quickly to local conditions, could be useful in data processing where noise terms can be replaced with useful estimates of their values.[#item_full_content]
Blockchain technologies are digital systems that work by distributing copies of information across several computers, also referred to as nodes, all of which are connected to a common network. These technologies underpin the trading of cryptocurrencies, as well as the functioning of other emerging digital services.Blockchain technologies are digital systems that work by distributing copies of information across several computers, also referred to as nodes, all of which are connected to a common network. These technologies underpin the trading of cryptocurrencies, as well as the functioning of other emerging digital services.[#item_full_content]
Over the past decades, computer scientists have developed many computational tools that can analyze and interpret images. These tools have proved useful for a broad range of applications, including robotics, autonomous driving, health care, manufacturing and even entertainment.Over the past decades, computer scientists have developed many computational tools that can analyze and interpret images. These tools have proved useful for a broad range of applications, including robotics, autonomous driving, health care, manufacturing and even entertainment.[#item_full_content]
Altruism, the tendency to behave in ways that benefit others even if it comes at a cost to oneself, is a valuable human quality that can facilitate cooperation with others and promote meaningful social relationships. Behavioral scientists have been studying human altruism for decades, typically using tasks or games rooted in economics.Altruism, the tendency to behave in ways that benefit others even if it comes at a cost to oneself, is a valuable human quality that can facilitate cooperation with others and promote meaningful social relationships. Behavioral scientists have been studying human altruism for decades, typically using tasks or games rooted in economics.[#item_full_content]
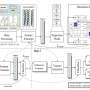
With the particular needs of scientists and engineers in mind, researchers at the Department of Energy’s Pacific Northwest National Laboratory have co-designed with Micron a new hardware-software architecture purpose-built for science.With the particular needs of scientists and engineers in mind, researchers at the Department of Energy’s Pacific Northwest National Laboratory have co-designed with Micron a new hardware-software architecture purpose-built for science.[#item_full_content]
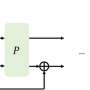
In computer security, random numbers are crucial values that must be unpredictable—such as secret keys or initialization vectors (IVs)—forming the foundation of security systems. To achieve this, deterministic random bit generators (DRBGs) are used, which produce numbers that appear random. However, existing DRBGs had limitations in both security (unpredictability against hacking) and output speed.In computer security, random numbers are crucial values that must be unpredictable—such as secret keys or initialization vectors (IVs)—forming the foundation of security systems. To achieve this, deterministic random bit generators (DRBGs) are used, which produce numbers that appear random. However, existing DRBGs had limitations in both security (unpredictability against hacking) and output speed.[#item_full_content]
Yiming Zhang didn’t grow up playing chess. Like many other people, the Carnegie Mellon University Ph.D. student discovered the Netflix series “The Queen’s Gambit” during the pandemic and began playing online. However, he quickly realized how unnatural it felt playing against chess bots.Yiming Zhang didn’t grow up playing chess. Like many other people, the Carnegie Mellon University Ph.D. student discovered the Netflix series “The Queen’s Gambit” during the pandemic and began playing online. However, he quickly realized how unnatural it felt playing against chess bots.[#item_full_content]
Storm surges or collapsing dams—authentic simulations of water flows are not only important for special effects in disaster movies, but could also help to protect coastal regions. For more realistic simulations of fluid motions, researchers at the Technical University of Munich (TUM) have developed a new method that also takes into account the interaction with air. The approach is so efficient that calculations of complex wave motions can even be carried out with standard computers.Storm surges or collapsing dams—authentic simulations of water flows are not only important for special effects in disaster movies, but could also help to protect coastal regions. For more realistic simulations of fluid motions, researchers at the Technical University of Munich (TUM) have developed a new method that also takes into account the interaction with air. The approach is so efficient that calculations of complex wave motions can even be carried out with standard computers.[#item_full_content]