In a world increasingly shaped by artificial intelligence, the question of how machines make decisions under uncertain conditions grows more urgent every day.In a world increasingly shaped by artificial intelligence, the question of how machines make decisions under uncertain conditions grows more urgent every day.[#item_full_content]
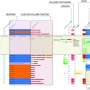
Tabular data is at the heart of scientific analysis—whether in medicine, the social sciences, or even archaeology. Making it comprehensible and usable is often a tedious task, especially when the data is extensive or complex. The Institute for Artificial Intelligence in Medicine (IKIM) at the University of Duisburg-Essen has developed an elegant solution: Datavzrd.Tabular data is at the heart of scientific analysis—whether in medicine, the social sciences, or even archaeology. Making it comprehensible and usable is often a tedious task, especially when the data is extensive or complex. The Institute for Artificial Intelligence in Medicine (IKIM) at the University of Duisburg-Essen has developed an elegant solution: Datavzrd.[#item_full_content]
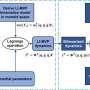
A research team from the Ningbo Institute of Materials Technology and Engineering (NIMTE) of the Chinese Academy of Sciences has developed a new method to enhance the efficiency of dynamics modeling for industrial robots, tackling long-standing bottlenecks in real-time torque computation.A research team from the Ningbo Institute of Materials Technology and Engineering (NIMTE) of the Chinese Academy of Sciences has developed a new method to enhance the efficiency of dynamics modeling for industrial robots, tackling long-standing bottlenecks in real-time torque computation.[#item_full_content]
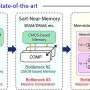
Organizing data in a specific order, also known as sorting, is a central computing operation performed by a wide range of systems. Conventional hardware systems rely on separate components to store and sort data, which limits their speed and energy efficiency.Organizing data in a specific order, also known as sorting, is a central computing operation performed by a wide range of systems. Conventional hardware systems rely on separate components to store and sort data, which limits their speed and energy efficiency.[#item_full_content]
Artificial intelligence chatbots are everywhere these days, from smartphone apps and customer service portals to online search engines. But what happens when these handy tools overestimate their own abilities?Artificial intelligence chatbots are everywhere these days, from smartphone apps and customer service portals to online search engines. But what happens when these handy tools overestimate their own abilities?[#item_full_content]
A study from EPFL reveals why humans excel at recognizing objects from fragments while AI struggles, highlighting the critical role of contour integration in human vision.A study from EPFL reveals why humans excel at recognizing objects from fragments while AI struggles, highlighting the critical role of contour integration in human vision.[#item_full_content]
AI image generation—which relies on neural networks to create new images from a variety of inputs, including text prompts—is projected to become a billion-dollar industry by the end of this decade. Even with today’s technology, if you wanted to make a fanciful picture of, say, a friend planting a flag on Mars or heedlessly flying into a black hole, it could take less than a second.AI image generation—which relies on neural networks to create new images from a variety of inputs, including text prompts—is projected to become a billion-dollar industry by the end of this decade. Even with today’s technology, if you wanted to make a fanciful picture of, say, a friend planting a flag on Mars or heedlessly flying into a black hole, it could take less than a second.[#item_full_content]
What began as a Ph.D. project has grown into a website with 120,000 unique visitors each year. With the platform OpenML, researcher Jan van Rijn is contributing to open science, aiming to make machine learning more transparent, accessible, and fair.What began as a Ph.D. project has grown into a website with 120,000 unique visitors each year. With the platform OpenML, researcher Jan van Rijn is contributing to open science, aiming to make machine learning more transparent, accessible, and fair.[#item_full_content]
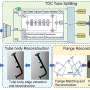
Complex tubes with flanges, joints and other components, characterized by a large number of diverse shapes and complex structures, are key parts of aircraft engines, rockets and other equipment. In order to ensure the smooth operation of this equipment, the dimensional accuracy of the tube must be ensured.Complex tubes with flanges, joints and other components, characterized by a large number of diverse shapes and complex structures, are key parts of aircraft engines, rockets and other equipment. In order to ensure the smooth operation of this equipment, the dimensional accuracy of the tube must be ensured.[#item_full_content]
As large language models (LLMs) like ChatGPT continue to advance, user expectations of them keep growing, including with respect to how quickly they can respond to our increasingly intricate prompts requesting answers to ever-challenging problems and tasks.As large language models (LLMs) like ChatGPT continue to advance, user expectations of them keep growing, including with respect to how quickly they can respond to our increasingly intricate prompts requesting answers to ever-challenging problems and tasks.[#item_full_content]