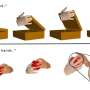
A technology that enables precise 3D motion with simple text input, without the need for complex initial settings, has been developed by Professor Seungryul Baek and his research team in Artificial Intelligence Graduate School at UNIST.A technology that enables precise 3D motion with simple text input, without the need for complex initial settings, has been developed by Professor Seungryul Baek and his research team in Artificial Intelligence Graduate School at UNIST.[#item_full_content]
In recent decades, many engineers have started developing artificial intelligence (AI)-based tools that can support the work of creative professionals, speeding up or enhancing the production of different types of content. These include computational models that can generate musical tracks and facilitate some aspects of music production.In recent decades, many engineers have started developing artificial intelligence (AI)-based tools that can support the work of creative professionals, speeding up or enhancing the production of different types of content. These include computational models that can generate musical tracks and facilitate some aspects of music production.[#item_full_content]
Computers have come so far in terms of their power and potential, rivaling and even eclipsing human brains in their ability to store and crunch data, make predictions and communicate. But there is one domain where human brains continue to dominate: energy efficiency.Computers have come so far in terms of their power and potential, rivaling and even eclipsing human brains in their ability to store and crunch data, make predictions and communicate. But there is one domain where human brains continue to dominate: energy efficiency.[#item_full_content]
An Oregon State University doctoral student and researchers at Adobe have created a new, cost-effective training technique for artificial intelligence systems that aims to make them less socially biased.An Oregon State University doctoral student and researchers at Adobe have created a new, cost-effective training technique for artificial intelligence systems that aims to make them less socially biased.[#item_full_content]
Underlying all complex multiphysics simulations are even more complex mathematical algorithms that solve the equations describing movement of physical phenomena—for instance, the radiation diffusion and burning plasma processes inherent in fusion reactions. Preconditioned solvers are often used in these algorithms to transform a problem so that it quickly and accurately converges to a solution.Underlying all complex multiphysics simulations are even more complex mathematical algorithms that solve the equations describing movement of physical phenomena—for instance, the radiation diffusion and burning plasma processes inherent in fusion reactions. Preconditioned solvers are often used in these algorithms to transform a problem so that it quickly and accurately converges to a solution.[#item_full_content]
By giving artificial intelligence simple associative learning rules based on the brain circuits that allow a sea slug to forage—and augmenting it with better episodic memory, like that of an octopus—scientists have built an AI that can navigate new environments, seek rewards, map landmarks and overcome obstacles.By giving artificial intelligence simple associative learning rules based on the brain circuits that allow a sea slug to forage—and augmenting it with better episodic memory, like that of an octopus—scientists have built an AI that can navigate new environments, seek rewards, map landmarks and overcome obstacles.[#item_full_content]
Bearing the smiling face of one of Australia’s cutest marsupials is a device its creators are claiming as the world’s first consumer product in quantum computing technology.Bearing the smiling face of one of Australia’s cutest marsupials is a device its creators are claiming as the world’s first consumer product in quantum computing technology.[#item_full_content]
Image generator models—systems that produce new images based on textual descriptions—have become a common and well-known phenomenon in the past year. Their continuous improvement, largely relying on developments in the field of artificial intelligence, makes them an important resource in various fields.Image generator models—systems that produce new images based on textual descriptions—have become a common and well-known phenomenon in the past year. Their continuous improvement, largely relying on developments in the field of artificial intelligence, makes them an important resource in various fields.[#item_full_content]
Robots that can navigate various terrains both rapidly and efficiently could be highly advantageous, as they could successfully complete complex missions in challenging environments. For instance, these robots could help to monitor complex natural environments, such as forests, or could search for survivors after natural disasters.Robots that can navigate various terrains both rapidly and efficiently could be highly advantageous, as they could successfully complete complex missions in challenging environments. For instance, these robots could help to monitor complex natural environments, such as forests, or could search for survivors after natural disasters.[#item_full_content]
Quantum computing is a rapidly growing technology that utilizes the laws of quantum physics to solve complex computational problems that are extremely difficult for classical computing. Researchers worldwide have developed many quantum algorithms to take advantage of quantum computing, demonstrating significant improvements over classical algorithms.Quantum computing is a rapidly growing technology that utilizes the laws of quantum physics to solve complex computational problems that are extremely difficult for classical computing. Researchers worldwide have developed many quantum algorithms to take advantage of quantum computing, demonstrating significant improvements over classical algorithms.[#item_full_content]