No matter how much data they learn, why do artificial intelligence (AI) models often miss the mark on human intent? Conventional comparison learning, designed to help AI understand human preferences, has frequently led to confusion rather than clarity. A KAIST research team has now presented a new learning solution that allows AI to accurately learn human preferences even with limited data by assigning it a “private tutor.”No matter how much data they learn, why do artificial intelligence (AI) models often miss the mark on human intent? Conventional comparison learning, designed to help AI understand human preferences, has frequently led to confusion rather than clarity. A KAIST research team has now presented a new learning solution that allows AI to accurately learn human preferences even with limited data by assigning it a “private tutor.”[#item_full_content]
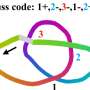
Today’s artificial intelligence models can’t even tie their own shoes.Today’s artificial intelligence models can’t even tie their own shoes.[#item_full_content]
Researchers at TU Wien have discovered an unexpected connection between two very different areas of artificial intelligence: Large Language Models (LLMs) can help solve logical problems—without actually “understanding” them.Researchers at TU Wien have discovered an unexpected connection between two very different areas of artificial intelligence: Large Language Models (LLMs) can help solve logical problems—without actually “understanding” them.[#item_full_content]
If you open a banking app, play a mobile game or scroll through a news feed every day while riding the bus, your commuting routine is probably bolstering your smartphone habit, according to new research that shows phone tendencies are stronger in locations chosen automatically.If you open a banking app, play a mobile game or scroll through a news feed every day while riding the bus, your commuting routine is probably bolstering your smartphone habit, according to new research that shows phone tendencies are stronger in locations chosen automatically.[#item_full_content]
When scientists test algorithms that sort or classify data, they often turn to a trusted tool called Normalized Mutual Information (or NMI) to measure how well an algorithm’s output matches reality. But according to new research, that tool may not be as reliable as many assume.When scientists test algorithms that sort or classify data, they often turn to a trusted tool called Normalized Mutual Information (or NMI) to measure how well an algorithm’s output matches reality. But according to new research, that tool may not be as reliable as many assume.[#item_full_content]
As language models (LMs) improve at tasks like image generation, trivia questions, and simple math, you might think that human-like reasoning is around the corner. In reality, they still trail us by a wide margin on complex tasks. Try playing Sudoku with one, for instance, where you fill in numbers one through nine in such a way that each appears only once across the columns, rows, and sections of a nine-by-nine grid. Your AI opponent will either fail to fill in boxes on its own or do so inefficiently, although it can verify if you’ve filled yours out correctly.As language models (LMs) improve at tasks like image generation, trivia questions, and simple math, you might think that human-like reasoning is around the corner. In reality, they still trail us by a wide margin on complex tasks. Try playing Sudoku with one, for instance, where you fill in numbers one through nine in such a way that each appears only once across the columns, rows, and sections of a nine-by-nine grid. Your AI opponent will either fail to fill in boxes on its own or do so inefficiently, although it can verify if you’ve filled yours out correctly.[#item_full_content]
Large language models (LLMs), artificial intelligence (AI) systems that can process and generate texts in various languages, are now widely used worldwide to create written content, source information and even to code websites or applications. While these models have improved significantly over the past couple of years, their answers can sometimes contain factual inaccuracies or logical inconsistencies.Large language models (LLMs), artificial intelligence (AI) systems that can process and generate texts in various languages, are now widely used worldwide to create written content, source information and even to code websites or applications. While these models have improved significantly over the past couple of years, their answers can sometimes contain factual inaccuracies or logical inconsistencies.[#item_full_content]
A research team led by Professor Jaesik Choi of KAIST’s Kim Jaechul Graduate School of AI, in collaboration with KakaoBank Corp, has developed an accelerated explanation technology that can explain the basis of an artificial intelligence (AI) model’s judgment in real-time.A research team led by Professor Jaesik Choi of KAIST’s Kim Jaechul Graduate School of AI, in collaboration with KakaoBank Corp, has developed an accelerated explanation technology that can explain the basis of an artificial intelligence (AI) model’s judgment in real-time.[#item_full_content]
Artificial intelligence is increasingly used to integrate and analyze multiple types of data formats, such as text, images, audio and video. One challenge slowing advances in multimodal AI, however, is the process of choosing the algorithmic method best aligned to the specific task an AI system needs to perform.Artificial intelligence is increasingly used to integrate and analyze multiple types of data formats, such as text, images, audio and video. One challenge slowing advances in multimodal AI, however, is the process of choosing the algorithmic method best aligned to the specific task an AI system needs to perform.[#item_full_content]
MIT researchers have developed a method that generates more accurate uncertainty measures for certain types of estimation. This could help improve the reliability of data analyses in areas like economics, epidemiology, and environmental sciences.MIT researchers have developed a method that generates more accurate uncertainty measures for certain types of estimation. This could help improve the reliability of data analyses in areas like economics, epidemiology, and environmental sciences.[#item_full_content]