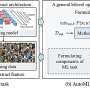
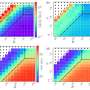
Recently, professors Risheng Liu from Dalian University of Technology and Zhouchen Lin from Peking University collaborated on an opinion article published in the National Science Review (NSR). Their article delves deeply into AutoML from the perspective of bilevel optimization, achieving unified modeling of various AutoML tasks while exploring challenges and opportunities. This article will be included in the NSR’s special topic on “Automating Machine Learning.”Recently, professors Risheng Liu from Dalian University of Technology and Zhouchen Lin from Peking University collaborated on an opinion article published in the National Science Review (NSR). Their article delves deeply into AutoML from the perspective of bilevel optimization, achieving unified modeling of various AutoML tasks while exploring challenges and opportunities. This article will be included in the NSR’s special topic on “Automating Machine Learning.”[#item_full_content]
Though artificial intelligence decreases human error in experimentation, human experts outperform AI when identifying causation or working with small data sets.Though artificial intelligence decreases human error in experimentation, human experts outperform AI when identifying causation or working with small data sets.[#item_full_content]
In an era where artificial intelligence (AI) is transforming industries from health care to finance, understanding how these digital brains learn is more crucial than ever. Now, two researchers from EPFL, Antonia Sclocchi and Matthieu Wyart, have shed light on this process, focusing on a popular method known as Stochastic Gradient Descent (SGD).In an era where artificial intelligence (AI) is transforming industries from health care to finance, understanding how these digital brains learn is more crucial than ever. Now, two researchers from EPFL, Antonia Sclocchi and Matthieu Wyart, have shed light on this process, focusing on a popular method known as Stochastic Gradient Descent (SGD).[#item_full_content]
Pollsters trying to predict presidential election results and physicists searching for distant exoplanets have at least one thing in common: They often use a tried-and-true scientific technique called Bayesian inference.Pollsters trying to predict presidential election results and physicists searching for distant exoplanets have at least one thing in common: They often use a tried-and-true scientific technique called Bayesian inference.[#item_full_content]
Researchers at the University of Trento, Italy, have developed a novel approach for prime factorization via quantum annealing, leveraging a compact modular encoding paradigm and enabling the factorization of large numbers using D-Wave quantum devices.Researchers at the University of Trento, Italy, have developed a novel approach for prime factorization via quantum annealing, leveraging a compact modular encoding paradigm and enabling the factorization of large numbers using D-Wave quantum devices.[#item_full_content]
About a quarter of Americans get their news on YouTube. With its billions of users and hours upon hours of content, YouTube is one the largest online media platforms in the world.About a quarter of Americans get their news on YouTube. With its billions of users and hours upon hours of content, YouTube is one the largest online media platforms in the world.[#item_full_content]
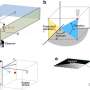
After a recent car crash, John Murray-Bruce wished he could have seen the other car coming. The crash reaffirmed the USF assistant professor of computer science and engineering’s mission to create a technology that could do just that: See around obstacles and ultimately expand one’s line of vision.After a recent car crash, John Murray-Bruce wished he could have seen the other car coming. The crash reaffirmed the USF assistant professor of computer science and engineering’s mission to create a technology that could do just that: See around obstacles and ultimately expand one’s line of vision.[#item_full_content]
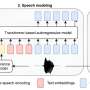
A team of artificial intelligence researchers at Amazon AGI announced the development of what they are describing as the largest text-to-speech model ever made. By largest, they mean having the most parameters and using the largest training dataset. They have published a paper on the arXiv preprint server describing how the model was developed and trained.A team of artificial intelligence researchers at Amazon AGI announced the development of what they are describing as the largest text-to-speech model ever made. By largest, they mean having the most parameters and using the largest training dataset. They have published a paper on the arXiv preprint server describing how the model was developed and trained.[#item_full_content]
How much cooler would basketball footage be if software could automatically shine a spotlight on key players? How much easier would it be to understand plays if arrows could indicate movement before the players actually move? How much improvement would be possible if one could see how distance from a basket affects shot trajectory?How much cooler would basketball footage be if software could automatically shine a spotlight on key players? How much easier would it be to understand plays if arrows could indicate movement before the players actually move? How much improvement would be possible if one could see how distance from a basket affects shot trajectory?[#item_full_content]
Machine learning researchers at Apple have developed an application that can accept a simple drawing and a text description to animate the drawing in desired ways. Tiffany Tseng, Ruijia Cheng and Jeffrey Nichols have published a paper describing the new app, called Keyframer, on the arXiv preprint server.Machine learning researchers at Apple have developed an application that can accept a simple drawing and a text description to animate the drawing in desired ways. Tiffany Tseng, Ruijia Cheng and Jeffrey Nichols have published a paper describing the new app, called Keyframer, on the arXiv preprint server.[#item_full_content]