A London court on Friday ruled that a British tabloid newspaper hacked Prince Harry’s phone while reporting on the royal family.A London court on Friday ruled that a British tabloid newspaper hacked Prince Harry’s phone while reporting on the royal family.[#item_full_content]
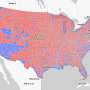
Virginia Tech researchers have discovered limitations in ChatGPT’s capacity to provide location-specific information about environmental justice issues. Their findings, published in the journal Telematics and Informatics, suggest the potential for geographic biases existing in current generative artificial intelligence (AI) models.Virginia Tech researchers have discovered limitations in ChatGPT’s capacity to provide location-specific information about environmental justice issues. Their findings, published in the journal Telematics and Informatics, suggest the potential for geographic biases existing in current generative artificial intelligence (AI) models.[#item_full_content]
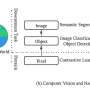
Imagine you are scrolling through the photos on your phone and you come across an image that at first you can’t recognize. It looks like maybe something fuzzy on the couch; could it be a pillow or a coat? After a couple of seconds it clicks—of course! That ball of fluff is your friend’s cat, Mocha. While some of your photos could be understood in an instant, why was this cat photo much more difficult?Imagine you are scrolling through the photos on your phone and you come across an image that at first you can’t recognize. It looks like maybe something fuzzy on the couch; could it be a pillow or a coat? After a couple of seconds it clicks—of course! That ball of fluff is your friend’s cat, Mocha. While some of your photos could be understood in an instant, why was this cat photo much more difficult?[#item_full_content]
Transformer architectures have facilitated the development of large-scale and general-purpose sequence models for prediction tasks in natural language processing and computer vision, for example, GPT-3 and Swin Transformer.Transformer architectures have facilitated the development of large-scale and general-purpose sequence models for prediction tasks in natural language processing and computer vision, for example, GPT-3 and Swin Transformer.[#item_full_content]
A research team led by Prof. Sun Zhong at Peking University has reported an analog hardware solution for real-time compressed sensing recovery. It has been published as an article titled, “In-memory analog solution of compressed sensing recovery in one step” in Science Advances.A research team led by Prof. Sun Zhong at Peking University has reported an analog hardware solution for real-time compressed sensing recovery. It has been published as an article titled, “In-memory analog solution of compressed sensing recovery in one step” in Science Advances.[#item_full_content]
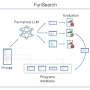
A team of computer scientists at Google’s DeepMind project in the U.K., working with a colleague from the University of Wisconsin-Madison and another from Université de Lyon, has developed a computer program that combines a pretrained large language model (LLM) with an automated “evaluator” to produce solutions to problems in the form of computer code.A team of computer scientists at Google’s DeepMind project in the U.K., working with a colleague from the University of Wisconsin-Madison and another from Université de Lyon, has developed a computer program that combines a pretrained large language model (LLM) with an automated “evaluator” to produce solutions to problems in the form of computer code.[#item_full_content]
In geospatial exploration, the quest for efficient identification of regions of interest has recently taken a leap forward with visual active search (VAS). This modeling framework uses visual cues to guide exploration with potential applications that range from wildlife poaching detection to search-and-rescue missions to the identification of illegal trafficking activities.In geospatial exploration, the quest for efficient identification of regions of interest has recently taken a leap forward with visual active search (VAS). This modeling framework uses visual cues to guide exploration with potential applications that range from wildlife poaching detection to search-and-rescue missions to the identification of illegal trafficking activities.[#item_full_content]
Eyewitness statements are one of the key sources for identifying perpetrators—and one of the most error-prone. For example, the Innocence Project—an organization that works to clear up miscarriages of justice in the U.S.—states that incorrect eyewitness statements played a role in 64% of the cases in which it was able to secure the release of people who had been wrongly convicted. Further research is needed to find out why eyewitnesses are so often wrong, and this will require extensive visual material.Eyewitness statements are one of the key sources for identifying perpetrators—and one of the most error-prone. For example, the Innocence Project—an organization that works to clear up miscarriages of justice in the U.S.—states that incorrect eyewitness statements played a role in 64% of the cases in which it was able to secure the release of people who had been wrongly convicted. Further research is needed to find out why eyewitnesses are so often wrong, and this will require extensive visual material.[#item_full_content]
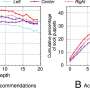
YouTube tends to recommend videos that are similar to what people have already watched. New research has found that those recommendations can lead users down a rabbit hole of extremist political content.YouTube tends to recommend videos that are similar to what people have already watched. New research has found that those recommendations can lead users down a rabbit hole of extremist political content.[#item_full_content]
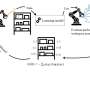
To effectively assist humans in real-world settings, robots should be able to learn new skills and adapt their actions based on what users require them to do at different times. One way to achieve this would be to design computational approaches that allow robots to learn from human demonstrations, for instance observing videos of a person washing dishes and learning to repeat the same sequence of actions.To effectively assist humans in real-world settings, robots should be able to learn new skills and adapt their actions based on what users require them to do at different times. One way to achieve this would be to design computational approaches that allow robots to learn from human demonstrations, for instance observing videos of a person washing dishes and learning to repeat the same sequence of actions.[#item_full_content]