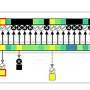
Adopting digital twin technology to manage the power consumption of idle devices could save organizations thousands of pounds a year and help reduce their carbon footprint, new research suggests.Adopting digital twin technology to manage the power consumption of idle devices could save organizations thousands of pounds a year and help reduce their carbon footprint, new research suggests.[#item_full_content]
Future events such as the weather or satellite trajectories are computed in tiny time steps, so the computation must be both efficient and as accurate as possible at each step lest errors pile up. A Kobe University team has introduced a new method that uses deep learning for creating tailored, accurate simulations that respect physical laws, while also being more computationally efficient.Future events such as the weather or satellite trajectories are computed in tiny time steps, so the computation must be both efficient and as accurate as possible at each step lest errors pile up. A Kobe University team has introduced a new method that uses deep learning for creating tailored, accurate simulations that respect physical laws, while also being more computationally efficient.[#item_full_content]
A new report from the University of Liverpool and the United Nations Migration Agency–International Organization for Migration (IOM) demonstrates how harnessing digital data collected from mobile phone applications and social media platforms can transform the way humanitarian agencies track and respond to population displacement during crises.A new report from the University of Liverpool and the United Nations Migration Agency–International Organization for Migration (IOM) demonstrates how harnessing digital data collected from mobile phone applications and social media platforms can transform the way humanitarian agencies track and respond to population displacement during crises.[#item_full_content]
A paper co-authored by Prof. Alex Lew has been selected as one of four “Outstanding Papers” at this year’s Conference on Language Modeling (COLM 2025), held in Montreal in October.A paper co-authored by Prof. Alex Lew has been selected as one of four “Outstanding Papers” at this year’s Conference on Language Modeling (COLM 2025), held in Montreal in October.[#item_full_content]
To make large language models (LLMs) more accurate when answering harder questions, researchers can let the model spend more time thinking about potential solutions.To make large language models (LLMs) more accurate when answering harder questions, researchers can let the model spend more time thinking about potential solutions.[#item_full_content]
In the nine years since TikTok debuted, it’s helped transform the way people view and absorb information, along with other short-form video platforms such as Instagram and Snapchat. Every month, TikTok alone has nearly 1.6 billion active users globally.In the nine years since TikTok debuted, it’s helped transform the way people view and absorb information, along with other short-form video platforms such as Instagram and Snapchat. Every month, TikTok alone has nearly 1.6 billion active users globally.[#item_full_content]
In April, OpenAI’s popular ChatGPT hit a milestone of a billion active weekly users, as artificial intelligence continued its explosion in popularity.In April, OpenAI’s popular ChatGPT hit a milestone of a billion active weekly users, as artificial intelligence continued its explosion in popularity.[#item_full_content]
Developers can now integrate large language models directly into their existing software using a single line of code, with no manual prompt engineering required. The open-source framework, known as byLLM, automatically generates context-aware prompts based on the meaning and structure of the program, helping developers avoid hand-crafting detailed prompts, according to a conference paper presented at the SPLASH conference in Singapore in October 2025 and published in the Proceedings of the ACM on Programming Languages.Developers can now integrate large language models directly into their existing software using a single line of code, with no manual prompt engineering required. The open-source framework, known as byLLM, automatically generates context-aware prompts based on the meaning and structure of the program, helping developers avoid hand-crafting detailed prompts, according to a conference paper presented at the SPLASH conference in Singapore in October 2025 and published in the Proceedings of the ACM on Programming Languages.[#item_full_content]
Even networks long considered “untrainable” can learn effectively with a bit of a helping hand. Researchers at MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) have shown that a brief period of alignment between neural networks, a method they call guidance, can dramatically improve the performance of architectures previously thought unsuitable for modern tasks.Even networks long considered “untrainable” can learn effectively with a bit of a helping hand. Researchers at MIT’s Computer Science and Artificial Intelligence Laboratory (CSAIL) have shown that a brief period of alignment between neural networks, a method they call guidance, can dramatically improve the performance of architectures previously thought unsuitable for modern tasks.[#item_full_content]
A University of Texas at Dallas researcher and his collaborators have developed an artificial intelligence (AI)-assisted tool that makes it possible for visually impaired computer programmers to create, edit and verify 3D models independently.A University of Texas at Dallas researcher and his collaborators have developed an artificial intelligence (AI)-assisted tool that makes it possible for visually impaired computer programmers to create, edit and verify 3D models independently.[#item_full_content]