There could soon be a new way to interact with your favorite AI chatbots—through the clothing you wear. An international team of researchers has developed a voice-sensing fabric called A-Textile. This flexible patch of smart material turns everyday garments into a kind of microphone, allowing you to speak commands directly to what you’re wearing. This lets you communicate with AI systems such as ChatGPT or smart home devices.There could soon be a new way to interact with your favorite AI chatbots—through the clothing you wear. An international team of researchers has developed a voice-sensing fabric called A-Textile. This flexible patch of smart material turns everyday garments into a kind of microphone, allowing you to speak commands directly to what you’re wearing. This lets you communicate with AI systems such as ChatGPT or smart home devices.Hi Tech & Innovation[#item_full_content]
Injuries are an inevitable part of the NFL with all the high-speed collisions, crushing hits and high exertion necessary on every play.Injuries are an inevitable part of the NFL with all the high-speed collisions, crushing hits and high exertion necessary on every play.Machine learning & AI[#item_full_content]
Less than 4 days left: Visibility, traction, and growth start at your TechCrunch Disrupt 2025 exhibit table
Only 4 days left to amplify your brand to 10,000+ tech leaders with an exhibit table at TechCrunch Disrupt 2025. Grow your startup on October 27-29 in San Francisco. Book here.Only 4 days left to amplify your brand to 10,000+ tech leaders with an exhibit table at TechCrunch Disrupt 2025. Grow your startup on October 27-29 in San Francisco. Book here.[#item_full_content]
Save up to $624 on your TechCrunch Disrupt 2025 Pass before prices rise in less than 4 days
Only 4 days left to save up to $624 on your TechCrunch Disrupt 2025 pass. Join 10,000+ founders, investors, and operators for 200+ sessions, 250+ speakers, and Startup Battlefield 200. Register now
before prices rise — and save 30% on group passes, or half off a +1 pass.Only 4 days left to save up to $624 on your TechCrunch Disrupt 2025 pass. Join 10,000+ founders, investors, and operators for 200+ sessions, 250+ speakers, and Startup Battlefield 200. Register now
before prices rise — and save 30% on group passes, or half off a +1 pass.[#item_full_content]
FleetWorks raises $17M to match truckers with cargo faster
Co-founded by a former Uber Freight product manager, and backed by Uber’s lead seed investor, FleetWorks is quickly scooping up customers in the trucking world.Co-founded by a former Uber Freight product manager, and backed by Uber’s lead seed investor, FleetWorks is quickly scooping up customers in the trucking world.[#item_full_content]
Aquawise will show off its AI-driven water quality tech at TechCrunch Disrupt 2025
Aquawise uses satellite images and a physics-based AI model to monitor and predict water quality at aquaculture farms.Aquawise uses satellite images and a physics-based AI model to monitor and predict water quality at aquaculture farms.[#item_full_content]
A year after tech firm OpenAI roiled Hollywood with the release of its Sora AI video tool, Chief Executive Sam Altman was back—with a potentially groundbreaking update.A year after tech firm OpenAI roiled Hollywood with the release of its Sora AI video tool, Chief Executive Sam Altman was back—with a potentially groundbreaking update.Business[#item_full_content]
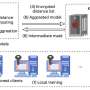
Federated learning is a machine learning technique that allows several individuals, dubbed “clients,” to collaboratively train a model, without sharing raw training data with each other. This “shared training” approach could be particularly advantageous for training machine learning models designed to complete tasks in financial and health care settings, without accessing people’s personal data.Federated learning is a machine learning technique that allows several individuals, dubbed “clients,” to collaboratively train a model, without sharing raw training data with each other. This “shared training” approach could be particularly advantageous for training machine learning models designed to complete tasks in financial and health care settings, without accessing people’s personal data.[#item_full_content]
India’s Airbound bags $8.65M to build rocket-like drones for one-cent deliveries
Lachy Groom backs Airbound in $8.65M seed round as it launches pilot in Bengaluru.Lachy Groom backs Airbound in $8.65M seed round as it launches pilot in Bengaluru.[#item_full_content]
California Governor Gavin Newsom on Monday signed into law a first-of-its-kind law regulating artificial intelligence chatbots, defying a push from the White House to leave such technology unchecked.California Governor Gavin Newsom on Monday signed into law a first-of-its-kind law regulating artificial intelligence chatbots, defying a push from the White House to leave such technology unchecked.Business[#item_full_content]