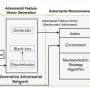
In recent years, cyber attackers have become increasingly skilled at circumventing security measures and successfully targeting technology users. Developing effective methods to detect, neutralize or mitigate the impact of these attacks is of utmost importance.In recent years, cyber attackers have become increasingly skilled at circumventing security measures and successfully targeting technology users. Developing effective methods to detect, neutralize or mitigate the impact of these attacks is of utmost importance.Security[#item_full_content]
HireBucket
Where Technology Meets Humanity